
Understanding Kerberos and cyber security
Author: Jon O’Reilly, Trustmarque Senior Penetration Tester
In the world of cyber security, network authentication plays a vital role in safeguarding your sensitive data and protecting against unauthorised access. One such authentication protocol that has gained significant popularity is Kerberos. Originally developed by the Massachusetts Institute of Technology (MIT), Kerberos offers a secure means of verifying users and services in a network environment, eliminating the need to transmit passwords in plain text. However, despite its robust design, Kerberos is not immune to exploitation.
In this blog post, we will delve into the inner workings of Kerberos, exploring its authentication process and shedding light on a specific vulnerability known as Kerberoasting. By understanding both the strengths and weaknesses of Kerberos, you can better equip yourself against potential threats and enhance your overall network security.
What is Kerberos?
Kerberos is a network authentication protocol, and its purpose is to securely authenticate users and services in a network without sending passwords in plain text. The protocol relies on a domain trusted third party, known as the Key Distribution Center (KDC), which issues time-sensitive tickets to authenticate users and services.
The Kerberos process
The Kerberos process can be broken down into the following steps:
1 – Authentication service request (AS-REQ): A user (or client) sends an authentication request to the KDC, including their username and the service they want to access.
2 – Authentication service response (AS-REP): If the KDC recognises the client’s username, it generates a Ticket-Granting Ticket (TGT) encrypted with the user’s password hash and returns it to the client.
3 – Ticket granting service request (TGS-REQ): The requesting client decrypts the TGT using their password, extracts a session key, and sends a new request to the KDC for a service ticket, including the TGT and the requested service’s identifier.
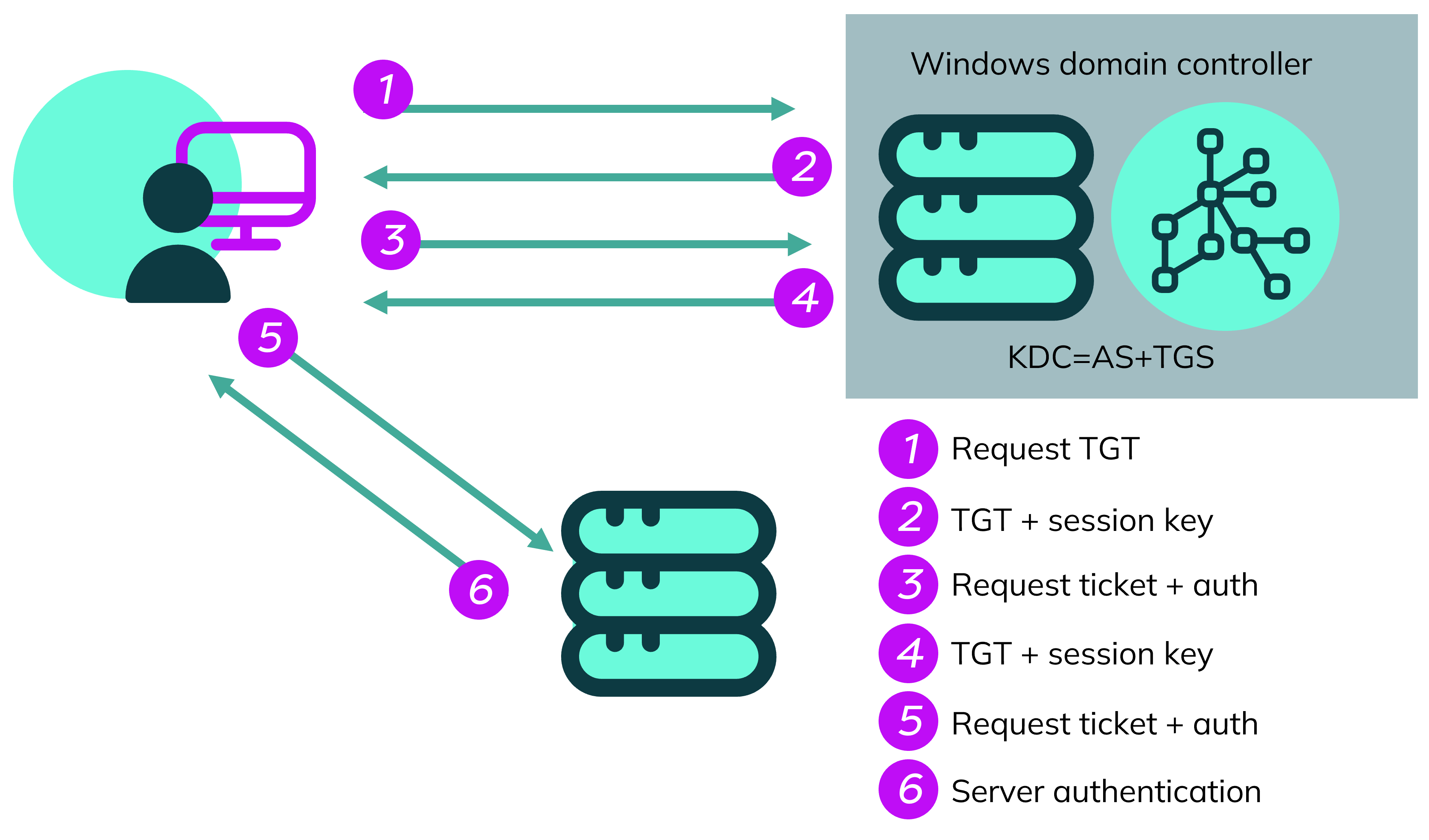
4 – Ticket granting service response (TGS-REP): The KDC validates the TGT, generates a service ticket encrypted with the service’s password hash, and sends it to the client.
5 – Access request (AP-REQ): The client presents the service ticket to the requested service, which decrypts the ticket to verify the client’s identity and grant access.
6 – Server authentication: User granted access.
Kerberos vulunerbilities
The Kerberos authentication protocol, which is widely implemented in Windows environments, can be exploited by attackers using a technique known as Kerbroasting.
Kerberoasting exploits the fact that service tickets are encrypted using the service’s password hash. Attackers with access to any domain account can request service tickets for any service in the network, even those they don’t have permission to access. This is made possible through the use of Service Principal Names (SPNs). Attackers target service accounts that have registered SPNs, because these accounts often hold higher privileges, potentially allowing unauthorised access to sensitive information.
From Kerberos to roasting
Kerberos is a crucial network authentication protocol that provides secure authentication for users and services within a network. Its reliance on a trusted Key Distribution Center ensures the confidentiality of passwords by eliminating the need to send them in plain text. However, like any system, Kerberos is not without its vulnerabilities.
In the second part this blog, we will explore the intricacies of Kerberoasting, examining how attackers exploit this vulnerability and the potential risks it poses to your network security. By understanding the inner workings of Kerberos and the techniques used to exploit it, you can better fortify your systems and take proactive measures to mitigate these risks.
Read part two: A guide to defending against Kerberoasting and what you can do
About the author: Jon O’Reilly is a Senior Penetration Tester at Trustmarque and currently holds CREST Certified Tester Infrastructure (CCT INF), with CHECK Team Leader status in infrastructure.


