
What is a Roast-in-the-Middle attack?
Roast-In-The-Middle is an innovative attack technique that targets a vulnerability in the Kerberos authentication protocol, specifically within the pre-authentication process. To confirm their identity and acquire a Ticket Granting Ticket (TGT) from the Key Distribution Center (KDC), a user must encrypt a timestamp using their secret key, which is derived from their password. If an attacker can intercept the encrypted timestamp by positioning themselves between the requesting user and the KDC, they can attempt to crack the user’s password offline, a method known as ASREQroasting.
Recent research by Charlie Clark (https://www.semperis.com/blog/new-attack-paths-as-requested-sts/) has discovered a new variation of this attack, in which attackers intercept the AS_REQ messages exchanged between the user and the KDC and replay them multiple times. By doing this, the attacker can request service tickets for other accounts with SPNs configured as long as they know the account names. This can be combined with SMB or LDAP null sessions to enumerate domain accounts. The attacker can then acquire the encrypted hash of the account’s password and use offline cracking tools to reveal the password itself. This new attack variation is dubbed ‘Roast-In-The-Middle’.
To execute the Roast-In-The-Middle attack, the attacker must intercept the AS_REQ messages between the user and the KDC. This can be achieved using methods such as ARP poisoning, ICMP redirect, or DHCPv6 spoofing to position themselves within the communication channel. Once the attacker captures the AS_REQ message, they can extract the encrypted timestamp and employ offline password-cracking tools to determine the user’s password.
Matt Creel has developed a tool called Roast-In-The-Middle based on Charlie Clark’s research. This tool automates the Roast-In-The-Middle attack process and can be used by attackers to exploit the Kerberos authentication protocol’s vulnerability. Creel’s blog post, “RITM In-Depth” (https://tw1sm.substack.com/p/roast-in-the-middle), provides further details about the tool.
How to carry out the attack:
sudo poetry run ritm -i eth1 -t <Target-device> -g <default-gateway> -u users –dc-ip <domain controller>
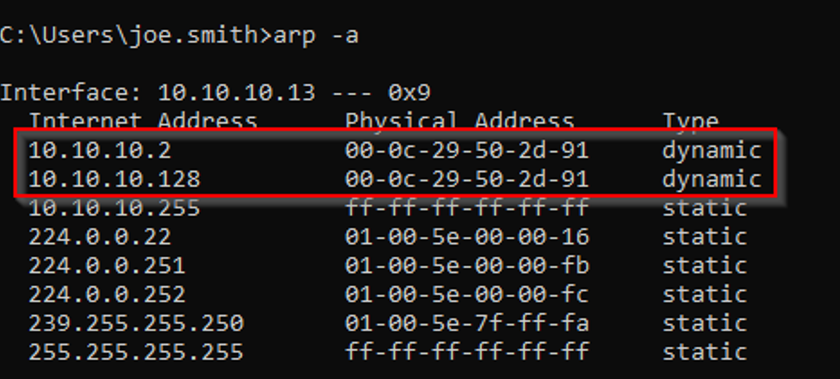
The Roast-In-The-Middle attack poisons ARP on the end user’s device, setting the domain controller MAC address to 00-0c-29-50-2d-91, which is the same MAC address as the attacking device on 10.10.10.128. This effectively forces any traffic from the end device to the domain controller to pass through the attacker’s machine, allowing the attacker to intercept and extract the encrypted timestamp from the AS_REQ messages sent during the Kerberos pre-authentication process.
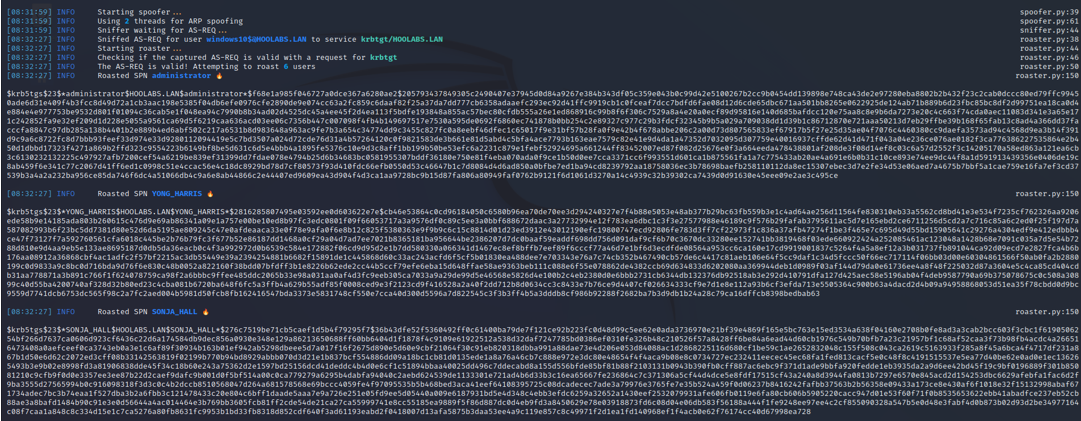
Once a man-in-the-middle stance has been established, the attacker simply bides their time, observing AS-REQs. As users’ TGTs expire and they request new ones from the domain controller, these requests are intercepted, as shown below. Additionally, tickets will be requested when users unlock their devices or when devices are restarted.
What we recommend:
- Monitor to detect anomalous Kerberos ticket requests, particularly focusing on Event ID 4768 in Windows event logs. This will aid in the early identification of potential Kerberoasting activities.
- Enforce robust password policies for service accounts. This involves setting complex, long, and unique passwords that are resistant to brute-force attacks, a common tactic in Kerberoasting.
- Strengthen network segregation strategies. This includes creating clearly defined network segments, particularly isolating critical infrastructure and sensitive systems. Implementing strict access controls ensures that only necessary communication between segments is allowed, thereby reducing the attack surface and limiting the potential impact of an ARP poisoning attack.


